Understanding the Lightning Network(2)
In the previous article, Understanding the Lightning Network(1) , we explored the operational principles of the Lightning Network (LN) and the security technologies behind bidirectional payment channels. Today, we continue to explain the concepts and technology that expand bidirectional payment channels into the full Lightning Network.
Expanding Bidirectional Payment Channels into the Lightning Network: Multi-hop Routing Technology
Using the example of Alice and Bob establishing a payment channel, what happens when others also want to join the Lightning Network? How can everyone be connected and enabled to make payments to anyone in the network?
To address this, we expand bidirectional payment channels into a full Lightning Network and use multi-hop routing. "Routing" in this context refers to finding paths within the network to complete a payment to a specific recipient.
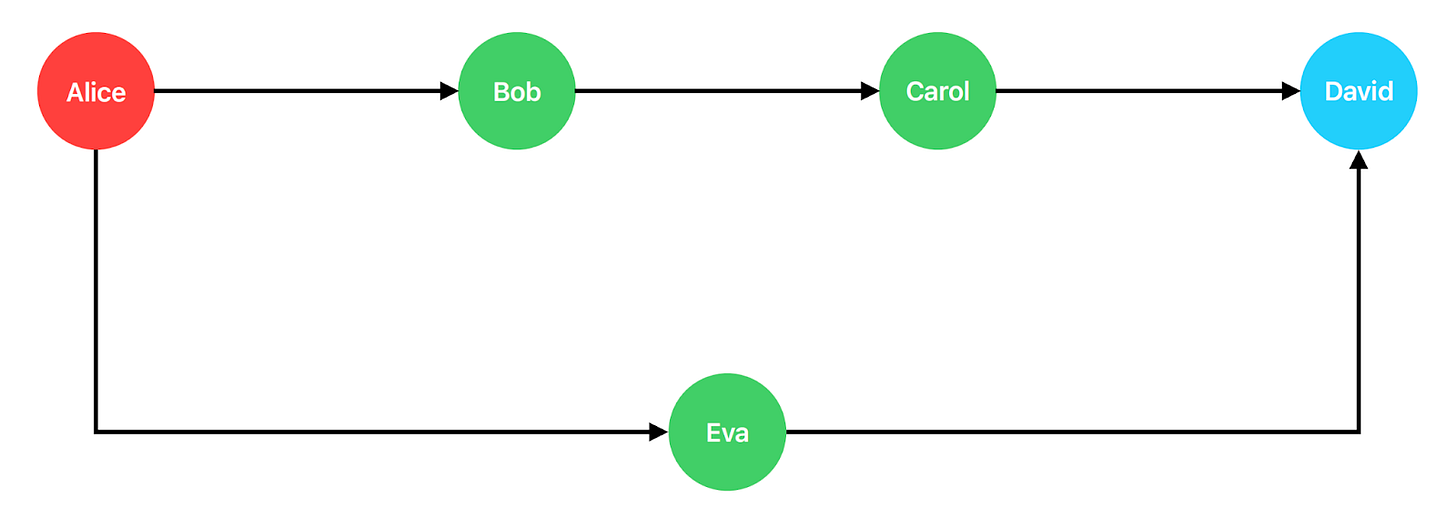
For example, suppose Alice wants to pay David 2,000 satoshis, but there’s no direct payment channel between them. However, there is a channel between Alice and Bob, Bob and Carol, and Carol and David. Alice could pay Bob, then Bob could pay Carol, and Carol could finally pay David—thus creating an indirect path to complete the payment. Here, Bob and Carol serve as routing nodes. If Alice also has a channel with Eva, who has one with David, she could alternatively send the payment via Eva and then to David.
Although the shortest path from Alice to David might appear optimal, in practice, the best route isn’t always the shortest one, as it depends on other factors like channel capacity, routing fees, and whether the routing nodes are online.
Popular Bitcoin LN implementations, like LND by Lightning Labs and CLN (Core Lightning) by Blockstream, use variants of Dijkstra’s algorithm for finding optimal routing paths, as does Nervos CKB's Fiber Network for Lightning.
Ensuring Routing Security: From HTLC to PTLC
In our example where Alice is paying David via intermediate nodes like Bob and Carol, how can we ensure that no node in the routing chain holds onto funds maliciously? Unlike traditional financial systems, which rely on trusted intermediaries, the Lightning Network is peer-to-peer, and we need a different way to secure transactions. This is where HTLCs (Hashed Time-Lock Contracts) come into play.
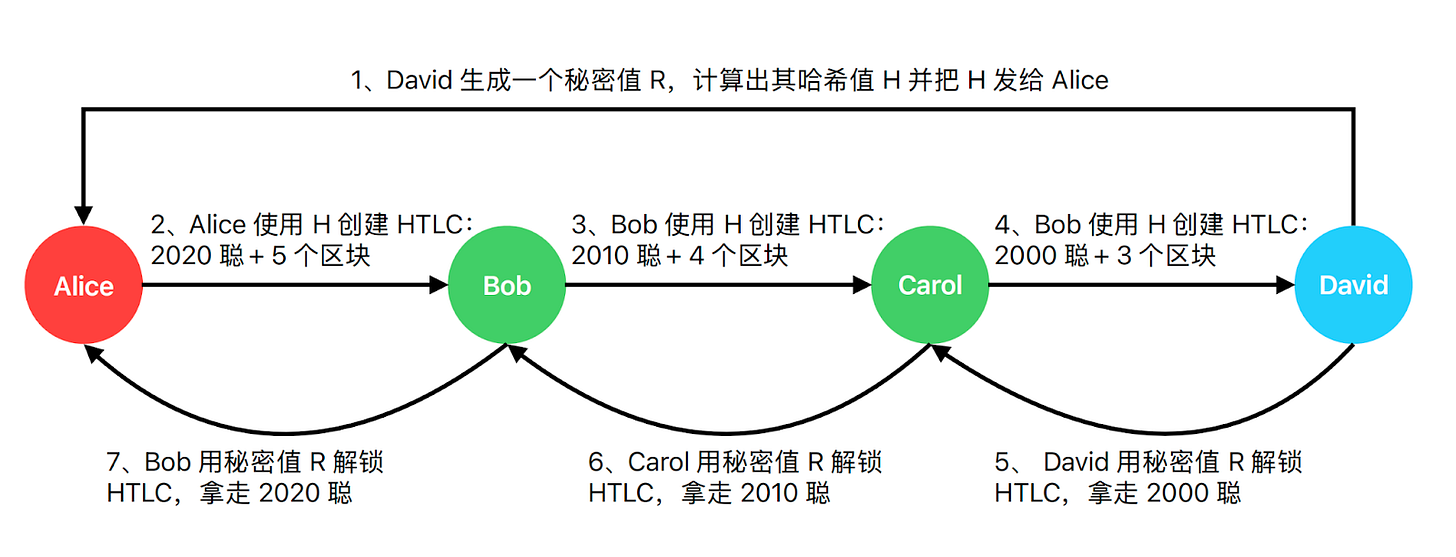
HTLCs consist of two parts: hash verification and expiry verification. To understand how HTLCs work, let’s look at Alice’s 2,000 satoshi payment to David, with Bob and Carol as routing nodes:
First, David needs to generate a secret value R, which can be any word or number. He then computes its hash value H and sends it to Alice. This hash value H will be placed in the locking script of the transaction output. Only the person who knows the secret value R corresponding to H can use this output. In the Lightning Network, R is referred to as the "preimage." If the secret value R is not revealed in time, the payment cannot proceed, and the sender will retrieve all the funds.
Next, Alice uses the received hash value H to create an HTLC, with a time lock set to the next 5 blocks, and the output amount is 2020 satoshis, where 20 satoshis are the routing fee for Bob. Simply put, Alice will pay Bob 2020 satoshis, as long as he can provide the secret value R within 5 blocks. Otherwise, the money will be returned to Alice.
Bob, in the channel between himself and Carol, creates an HTLC using the same hash value H that Alice provided, with a time lock set to the next 4 blocks, and the output amount is 2010 satoshis, where 10 satoshis are the routing fee for Carol. Simply put, Bob will pay Carol 2010 satoshis, as long as she can provide the secret value R within 4 blocks. Otherwise, the money will be returned to Bob.
Carol, in the channel between herself and David, creates an HTLC using the same hash value H, with a time lock set to the next 3 blocks, and the output amount is 2000 satoshis. Simply put, Carol will pay David 2000 satoshis, as long as he can provide the secret value R within 3 blocks. Otherwise, the money will be returned to Carol.
David then uses the secret value R to unlock the HTLC set by Carol and takes 2000 satoshis.
After David takes the funds, Carol also learns the secret value R. She uses R to unlock the HTLC set by Bob and takes 2010 satoshis.
After Carol takes the funds, Bob also obtains the secret value R. He uses R to unlock the HTLC set by Alice and takes 2020 satoshis.
Through this mechanism, Alice successfully paid David 2000 satoshis without the need to establish a direct payment channel. Throughout the process, no party needed to trust each other, and the routing nodes received their due fees. Even if the payment is interrupted at some point, thanks to the time-locking mechanism, no one will suffer any losses, and the funds will automatically return after the lock time expires.
However, HTLC poses a potential privacy issue: the same secret value (preimage) is used across the entire route. If an entity controls multiple nodes along the payment path, it could compare the inputs and outputs of different nodes to infer the full transaction details, potentially guessing the identities of both the payer and the payee. This weakens the privacy protection provided by onion routing in the Lightning Network.
To address this issue, the Bitcoin community proposed PTLC (Point Time Lock Contract). In the PTLC scheme, each hop along the path uses a different secret value. This way, the privacy provided by onion routing is preserved. The Lightning Network Fiber Network introduced by Nervos CKB plans to implement PTLC in the future, further enhancing privacy protection within the Lightning Network.
Conclusion:
As technology continues to advance, the Lightning Network is undergoing continuous optimization and improvement. From LN-Penalty to eltoo to Daric, from HTLC to PTLC, we are witnessing ongoing enhancements in the areas of security and privacy protection. In the future, with the adoption of more innovative technologies and the ecosystem’s development, the Lightning Network is poised to become a critical infrastructure driving the adoption of cryptocurrencies, contributing to the realization of a true P2P economy.